Mac Address Mask Calculator

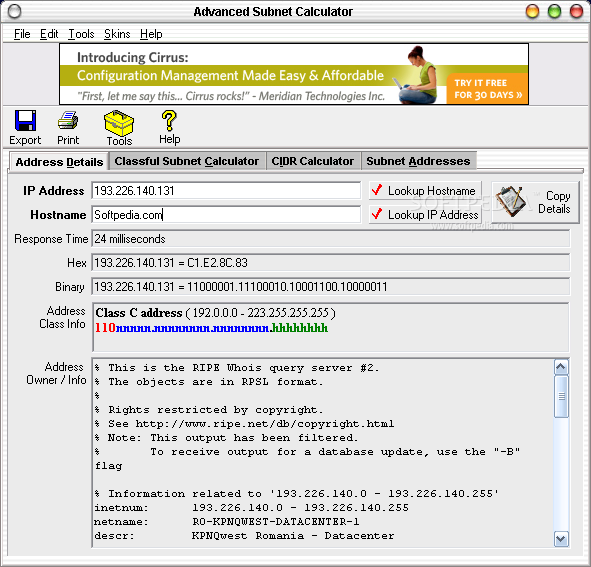
Standard syntax for writing IP addresses with a routing prefix. It consists of an IP address, a slash, then a number of bits to measure the routing prefix. The bits are applied to the address from left to right. 192.0.2.0/24 is an example of CIDR notation. Bit mask that can be used to define the network portion of an IP address. With a refreshed GUI, native Windows or Mac operation, and support for IPv6, the IP Subnet Calculator is perfect for quickly computing your subnet mask and address ranges, learning about IPv6, and supporting migration from IPv4 to IPv6. More Details: Automatic Subnet Calculations. This free online IP subnet calculator covers both IPv4 and IPv6 protocols, providing information such as IP address, network address, subnet mask, IP range, and more. Also, explore hundreds of other math, financial, fitness, and health calculators. The subnet calculator lets you enter a subnet range (CIDR) and see IP address information about that range You can type your range directly in CIDR notation, or use the optional Mask pull-down: 74.125.227.0/29 74.125.227.0, then select Optional Mask from dropdown.
- Mac Address Mask Calculator Excel
- Mac Address Mask Calculator Instructions
- Mac Address Mask Calculator Free
Exposing your MAC address is of course not a security issue if you assume that you have full control of your network. Meaning security is in place and you trust people who manage your network. But of course this is not always the case. Mostly, people connect (mostly via wi-fi) to public spaces like coffee shops, hotels, airport or other networks that they do not control. Doing this exposes your MAC address and in turn can be used to identify your computer and the user. You can change your MAC address by Technitium MAC Address Changer. You should keep in mind that changing your MAC address is by no means enough to make you completely anonymous. Check out the tools section for tips on how to do this.
While your MAC address is not permanently tied to your device's hardware, it will remain the same unless you change it yourself. As a result, it might allow someone to link your online activities, even if you take steps to keep them separate. If you sign into Facebook one day, for example, then return to the same network a week later to update your anonymous blog, anyone with access to the local network logs can easily learn that the same computer was used for both activities, even if you get a new IP address, use a different Web browser, clear your cookies, and sign in with a different username.
River belle casino canada. Mac powder foundation nw25. Mac os x yosemite user manual. Magnets and slot machines.Mac Address Mask Calculator Excel
Mac Address Mask Calculator Instructions
Mac Address Mask Calculator Free
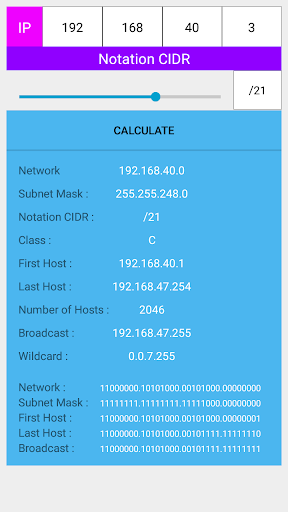 A subnet mask is always be a series of 1s, followed by a series of 0s.
A subnet mask is always be a series of 1s, followed by a series of 0s. 
Mac Address Mask Calculator
UNDER MAINTENANCE